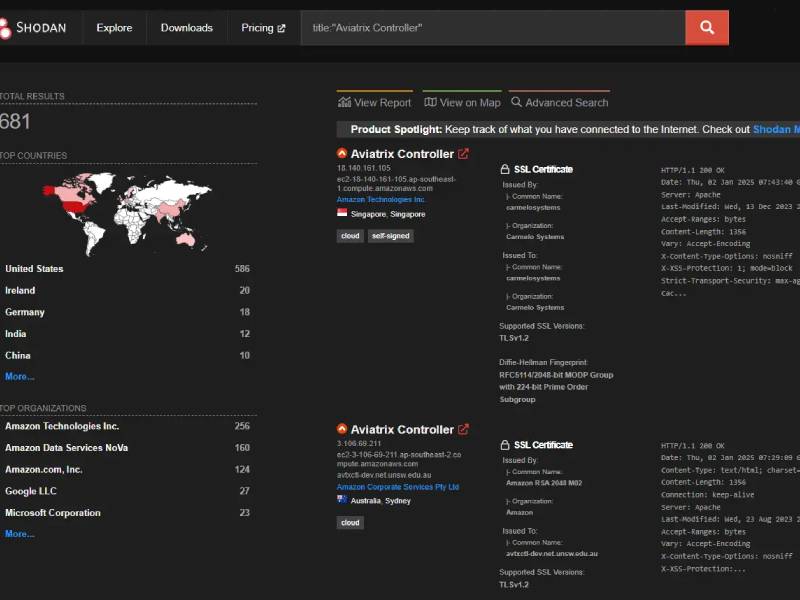
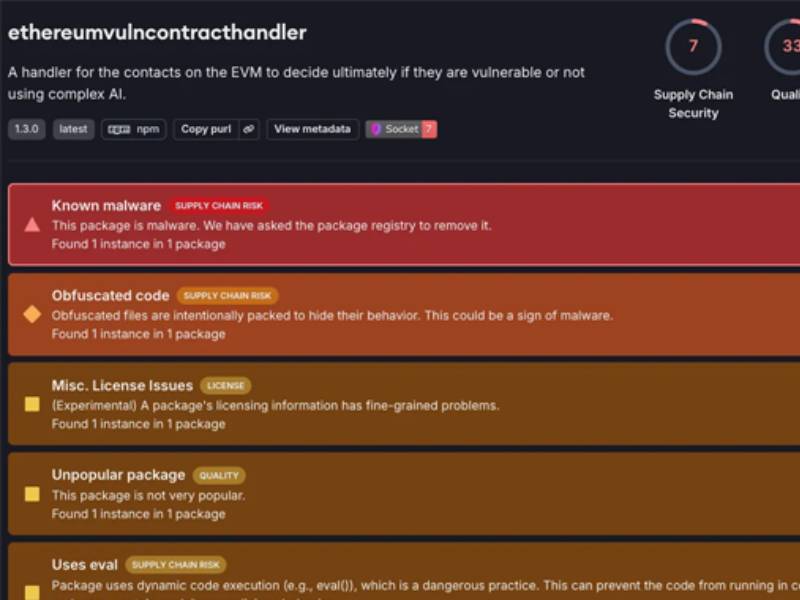
Darcula Adds GenAI to Phishing Toolkit, Lowering the Barrier for Cybercriminals
The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to their cybercrime suite with generative artificial intelligence (GenAI) capabilities.